Ransomware is becoming a growing problem, posing a massive threat to all computer users – particularly businesses with many users and shared network drives.
- Cryptolocker Virus For Testing Machine
- Cryptolocker Virus For Testing
- Cryptolocker Virus For Testing Machine

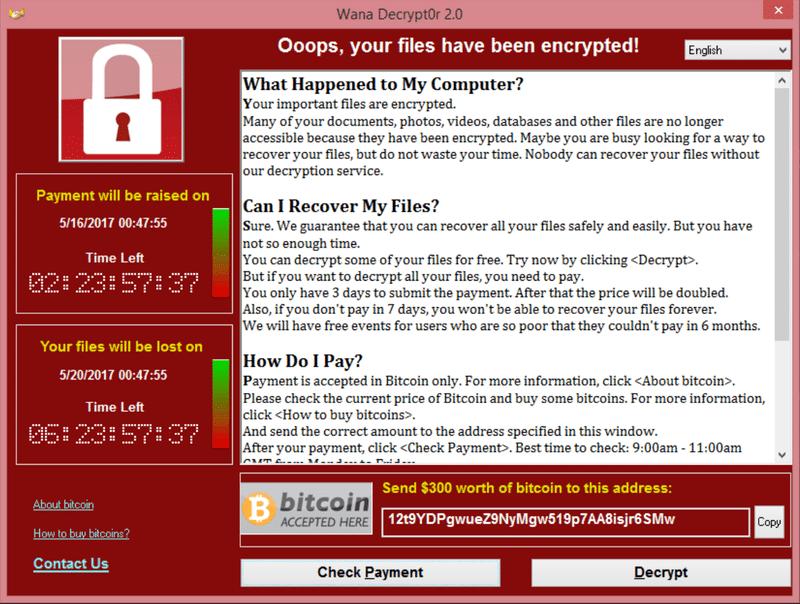
The typical ransomware starts with a user being invited to “open” a document, but what they don’t realise that it is actually a program that silently starts encrypting every document the user has access to- even if they don’t have admin-rights on the computer. Once the files are encrypted the user offered the chance to decrypt the files for a fee.
RanSim is a free tool for Windows that will simulate several ransom-ware style attacks and will let you know how vulnerable your computer is. Providing you the opportunity to test various anti-virus tools.
- Oct 18, 2013 If CryptoLocker is running and has already popped up its payment demand page, you can still remove it and clean up, but the Virus Removal Tool cannot decrypt your scrambled files – the contents.
- Generally, if someone gets a virus on their computer it's a pain in the ass but it's not threatening to the company on the whole. The computer is isolated and reinstalled or otherwise cleaned up, and you're off again. With Cryptolocker, 9 times out of 10 the person seems to also have a link to at least one network share.

RyptoLocker is a family of ransomware whose business model (yes, malware is a business to some!) is based on extorting money from users. This continues the trend started by another infamous piece of malware which also extorts its victims, the so-called ‘ Police Virus ’, which asks users to pay a ‘fine’ to unlock their computers.
It will ONLY simulate ransomware – it DOES NOT encrypt any files.
Cryptolocker Virus For Testing Machine
It tests vulnerability for:
Cryptolocker Virus For Testing
- InsideCryptor – encrypts files using strong encryption and overwrites most of the content of the original files with the encrypted data.
- LockyVariant – simulates the behavior of a recent version of Locky ransomware.
- Mover – Encrypts files in a different folder using strong encryption and safely deletes the original files.
- Replacer – Replaces the content of the original files. A real ransomware would show a message that fools users into thinking they can recover them.
- Streamer – Encrypts files and writes data into a single file, using strong encryption, then deletes the original files.
- StrongCryptor – Encrypts files using strong encryption and safely deletes the original files.
- StrongCryptorFast – Encrypts files using strong encryption and deletes the original files.
- StrongCrytptorNet – Encrypts files using strong encryption and deletes the original files. It also simulates sending the encryption key to a server using an HTTP connection.
- ThorVariant – Simulates the behavior of a recent version of Thor ransomware.
- WeakCryptor – Encrypts files using weak encryption and deletes the original files.
Cryptolocker Virus For Testing Machine
DOWNLOAD: From the developer (requires personal information provided in a form) or from Major Geeks mirror.